Data: The Dark (and Light) Side of Additive Manufacturing: AM Radio #41
Additive manufacturing relies on and creates large amounts of data. On AM Radio, Stephanie Hendrixson and Dr. Tim Simpson discuss concerns around protecting AM data, plus how data security can bring greater opportunities for this technology.
Share
As a “born digital” technology, additive manufacturing intrinsically relies on data, more so than any other manufacturing process. That data reliance potentially exposes AM users to data security and cybersecurity issues; efforts are underway to help these users protect designs, print parameters, machines and even 3D printed parts. But beyond the dark side of data, figuring out secure ways of storing and sharing data also opens the door to more freely distributing manufacturing, sharing material and print profiles, and flexible, secure supply chains. In this episode, I talk with Dr. Tim Simpson about all things AM and data.
Transcript
Stephanie Hendrixson 00:06
Additive manufacturing is data-driven manufacturing. That brings a lot of power and flexibility but also potentially makes additive data vulnerable to attack. In this episode, I talk with Tim Simpson about cybersecurity and data assurance for additive manufacturing. That's coming up on AM Radio.
Jodee McElfresh 00:26
This episode of AM Radio is brought to you by Formnext Forum: Austin, the first of a series of Formnext events coming to the United States, find more information at FormnextForum.com.
Stephanie Hendrixson 00:41
Welcome to AM Radio, the show where we tune in to what's happening with additive manufacturing. I'm Stephanie Hendrixson, with Additive Manufacturing Media, and I'm joined again by Dr. Tim Simpson. Hi, Tim.
Tim Simpson 00:50
Hey, how you doing, Stephanie?
Stephanie Hendrixson 00:52
Good. So today, I want to talk about something that we sort of started to discuss in a previous episode. So, in Episode 37, we were talking about sustainability. And I think kind of getting into like the distributed manufacturing and the ways that that can reduce carbon footprints. And that kind of led us into talking a little bit about cybersecurity and like, how do you protect your data when you're sending files to different locations? And we sort of teased that we wanted to have this cybersecurity, data focused conversation. And that's kind of the plan for today.
Tim Simpson 01:23
Yes, certainly, I think with additive being a, born a digital process, right, we're much more aware of how important the data is, both the data that is needed to drive and run the process as well as the data we get with the process. And of course, the data we need to compile after the process. So creates all sorts of new opportunities and new threats as well there that many manufacturers may or may not be aware of.
Stephanie Hendrixson 01:49
I guess that's kind of where I want to start. So additive is this, like, born digital process. But how different really, is it compared to CNC machining, compared to other types of manufacturing? Is it more vulnerable from your perspective? How different do you see it?
Tim Simpson 02:02
I think one of the differences with additive manufacturing compared to other processes is that we don't rely as heavily on some of the tooling, for instance, in many ways, the data is the tooling for additive manufacturing. And so the notion that if somebody has your data, they can turn around and print your parts. All they need is the material and the printer, etc., versus CNC machining, casting, forging, right, you need patterns, you need tools, you need hardware, to actually make the components. So yes, they have a, some of the same data susceptibility is there, in some ways, additive is a bit easier to hack and attack, just given the nature of the process.
Stephanie Hendrixson 02:42
Yeah, like that, we talked about additive manufacturing has this like low barrier to entry, because you don't have to get the tooling like you don't need all this other stuff. But that does make it maybe more vulnerable, easier to take a design and to recreate it if you don't also need the cutting tools or the mold or you know, whatever else goes along with it. But, I also think that there's a little bit of a mindset aspect of this. So one of the people that I talked to prior to this episode fairly recently is Brian Luffy. And he's the director of engineering at CyManII, which it's the Cybersecurity Manufacturing Innovation Institute, DOE-funded organization that's trying to help make manufacturing more secure. And I put this question to him and his comment was sort of like, well, AM isn't more vulnerable, necessarily, like most manufacturing these days has some digital element to it, it has some element of data. And he kind of made the point that in some ways, the additive users are a little bit easier to work with, because they're already used to seeing their data as an asset and seeing it as a potential risk factor. And so they're already sort of thinking of it as something that they need to protect
Tim Simpson 03:43
In that regard as well, I think one of the other challenges of additive is the ability to get in there, tweak and manipulate data during the process, how well can we detect and or identify 'Oh, something happened?' For instance, if we go in and, and hack an STL file, or if we change some process parameters, to what extent would you actually see that occur in the process that then could potentially lead to a failure, versus if you change, some G code settings in CNC, and all of a sudden, the machine tool crashes into something or doesn't cut enough, having used those processes longer, we have a better sense of what to look for, therefore, it's you know, the ability to detect and, and identify when things are, have gone correctly or incorrectly. We're, we're further along in that regard with more traditional processes compared to additive. So maybe it's both of those aspects, right? It's also the the reliance on data and then the ability to detect if and when something happens, sort of like standard failure mode effects analysis, right? How frequently is it going to happen? How easy is it to detect, right? And then what, what's the impact when it does happen? And you start looking at those and I think we're just lower on the maturity level across many of those when it comes to additive manufacturing. You did hack an STL file, you change some points on your polygon, you change this parameter setting. Is that going to cause a catastrophic failure? Maybe maybe not. We just we don't know yet, we don't have the data. It's still too young.
Stephanie Hendrixson 05:09
That's a really good point. Yeah, it's just, it's less mature. And so we don't have good ways necessarily of like measuring these things. Or maybe we don't even really know what we're looking for. So I want to talk about that for a minute. So you mentioned STL, and like the STL is obviously an important piece of data. But there's also the print parameters. But there's also like other things, you know, maybe with your printer performance, or other aspects, like what are all the different data things that additive manufacturers might need to be looking at?
Tim Simpson 05:38
Oh, good Lord, there's tons, tons and tons and tons of data. Actually, I was looking before, as we had talked about and prepped for this as well. NIST, for example, has been trying to come up with new standards for, for data, just data definitions when it comes out in manufacturing. Different manufacturers and OEMs call different process parameters different things, the type of data that we capture, the different sensor data. So, there is standard definitions now, there's actually a standard for data pedigree. So, the data we want to capture throughout the entire process that's now out there. And so the ability as well with additive, not only do we have all of the data for the process parameters, but now with qualification, certification, right, everybody's putting all these different sensors on there and monitoring this and monitoring that, you can get completely overwhelmed with terabytes of data for a single build or a single part. And so it's no longer just a simple, go-no go gauge. It's 'Hey, oh, here's four terabytes of data, go figure out if something was wrong.'
Stephanie Hendrixson 06:41
Yeah, that sounds like a job for AI rather than, rather than humans.
Tim Simpson 06:45
Absolutely, absolutely.
Stephanie Hendrixson 06:47
We're going to talk about kind of the negative aspects of data. But like, there are a lot of opportunities here, too, if you do have that record, you do have that data and you know, the important parts of it, that potentially makes your qualification process easier. One of the companies I wrote about recently is called VeriTX. And it's founded by this guy, James Regenor. And basically, they sort of started off thinking that this would be like a distributed manufacturing marketplace. And that's still kind of in the pipeline. But they've sort of shifted gears to be more of a data assurance company. So focusing on how do you lock down files? How do you let people securely transfer data like so if you're an OEM and you want to contract a supplier to do something without totally exposing your IP, they can help you do that. But one of the points that he made in that conversation was data, it seems like this negative thing, like you've got to protect it, you've got to secure it. But if you can find good ways of doing that, think about like how much easier the audit process would be how much less effort you would have to put in, how much less time and resource you would have to devote to just continually like going through audits, if you're like a certified supplier, if there was a way that everybody would trust, like, okay, yeah, you're making what you say you're making, you're doing it with the right process, everything is acting the way that it's supposed to.
Tim Simpson 08:01
Yeah, I think there's certainly there's value in the data, right? And so if you can capture that data and use that data, assure the data, show the pedigree, etc., then, you know, there's certainly value in that and I think people are willing to pay for it. You know, you're looking at what what Senvol has been doing, for example, with some of the data that they're now providing assurances through the work that they've done through various contracts and efforts and also as you were talking about VeriTX there made me think of Mike Vasquez's TRACEam program way back when was one of the first that I recall startup trying to, trying to put together just this, I got my, my CAD files, my STL files, my process parameter files, I got my run files, I got my build files, I got, you know, all of this. And the industry for many years has struggled with, how do we adapt PLM systems, ERP systems, whatever to capture and use all this data, which now is particularly if you're in a, in a highly regulated industry, FDA, FAA, etc., you have to have that data all the way throughout as part of the package for, for qual and cert. So it's been interesting, and I think good that we are shifting in that direction. And I think people are also seeing, as I said earlier, the value in having it and doing it well. And some of these solutions are coming at just the right time to help with the industrialization of additive manufacturing that I think's going on.
Stephanie Hendrixson 09:24
It's interesting, I think that kind of ties back to something I talked to CyManII about. They are obviously trying to assist, like with all types of manufacturing, but they have an additive user that they're working with. Additive company in the Midwest that's been hit with ransomware a couple of times, I think twice, and started working with CyManII kind of as a way of like, how do we, how do we protect ourselves from this happening again? And so this organization, they're looking at kind of the cybersecurity of their systems and their network and all of that stuff, but they're also approaching this from a real manufacturing perspective, like one of the things that they're working on right now is incorporating sensors on to the linear actuators of the 3D printers, which doesn't sound like a cybersecurity thing. And it's really a maintenance issue, but it's going to also offer some security aspects as well. So these linear actuators that they're replacing are in the tens of thousands of dollars, they're expensive. And they don't have a really great system for how and when to do this, like the oil change in your car. Do you do it every 3,000 miles regardless of whether or not you need it? Or do you wait for the check engine light to come on, and then like, it's an emergency at that point. And so by adding these sensors to their machines, they're gonna get to a point of more predictive maintenance, where they can be notified when the linear actuator is starting to wear when it is close to needing replaced, and you know, schedule that downtime. But it's also going to be like another check on the machine like is the machine making what it's supposed to be making? If something starts to go weird with the linear actuator, and it's not a maintenance issue, then maybe that's a red flag to say, Hey, something is different about this part file or something is different about the way this machine is operating. And like potentially, that is a security issue that needs to be patched.
Tim Simpson 11:01
It's almost like a two-factor authentification for your 3D printer, right?
Stephanie Hendrixson 11:06
So yeah, yeah.
Tim Simpson 11:07
Sending you that verification code, as well as your, is your linear actuator, your motors spinning the right amount of times, the right frequency, or whatever. So absolutely. And I think, you know, along those lines, printer farms and things we were setting up at Penn State years ago, the Maker Commons, so 32 Makerbots, that you know, all of our students could have free access to. But to your point, we were gathering those statistics on successes, failures, you know, replacements of cartridges, etc., that both became part of how do we, how do we keep this up and operational, but then became also useful data to understand sort of the overall efficiencies of that capability plus the individual printers plus everything else. And so there's value in that because now if you're thinking about the uptime on your printers, using that data to predict and prevent failures, so that when the end of the semester crunch happens, all 32 printers are up and running, versus all of a sudden not. So the data is certainly useful in many ways. We just, you know, again, when we talk cybersecurity, we see it as as a threat versus the value that can be created with that data.
Stephanie Hendrixson 12:19
Wow, it's like the ultimate stress test, like what happens with the printers during finals week? And like, are they all gonna be?
Tim Simpson 12:24
How do you balance, all of a sudden you have, you have 100,000 students that have free access to 3D printing in their classes and things? And so, yeah, how much can you really coordinate that or not. And so that's where we're actually in terms of the printer OS and some of these sort of distributed systems, whether it's for organizing your printers, organizing your parts, organizing your data, right, I think you're starting to see more and more of these coming online and available now to, again, try and streamline operations, try and make things more efficient, try and make things more effective, so that we all collectively have a better experience with, with 3D printing and additive manufacturing.
Stephanie Hendrixson 13:07
Yeah. And I think like that's kind of maybe where all this data stuff is headed like towards the distributed manufacturing model towards the quote unquote democratized manufacturing, can you allow people access to printers that they don't necessarily own, like, it's a student sending a file to the lab. I wrote about a company earlier this year called 3DOS, that's kind of their vision, whether you're an OEM and like you own the design, you've created this design, you own the IP, and you want to have it made close to your customer. Or if you're like a celebrity, or some other type of like creative person who just wants to develop a product, kind of put it out in the world, and maybe sort of like test the marketplace. The way they describe their model is, it's kind of like DoorDash, you, you can order something and then they'll just kind of like find the nearest DoorDasher, or find the nearest manufacturing facility that can make it for you, and send it out that way. And I think when we figure out ways of being able to protect the data, move it securely, and like trust it, a lot of those opportunities open up and I think we're kind of at the maybe just like the the very early stages of that.
Tim Simpson 14:12
Now, you brought up a good point there, right? It's all about trust. Do I trust that my additive process is producing the material and the part with the properties that I want? And now to what extent can that data establish that trust, and/or tell us when maybe we don't, we can't trust it because we've detected an anomaly or something else out there. But, but I think 3DOS and you know, even look at like, like Xometry and others, right? These distributed manufacturing now. So that's an advantage as well of additive being a digital process is that you can send that data file anywhere and with the right printer and the right material, turn around and print that part or those set of parts and things and so you are seeing different business models, different companies, startups, even established firms that are now trying to take full advantage of the digital data-driven processes that define additive manufacturing.
Stephanie Hendrixson 15:07
It's kind of an interesting paradox. Like if you figure out how to lock down your data in a secure enough way, it makes it much more open and like easier to share it.
Tim Simpson 15:15
Yeah. And I've actually heard with some of these new sort of additive marketplaces, right, you can come in and buy material properties or get access to it. I've even seen and heard of companies that have developed process parameter sets for, say, one material A and company over here has done material B. And they said, Hey, we've, we've done this, you did that? What if we swap and we both sort of win out of this, right? There's mutual benefit to sharing that data, say, within your supply chain, or between an OEM and some of its suppliers, for example, so that now the OEM can focus on some of the higher value add things and the supplier can be cranking out additive parts without having to invest hundreds or millions of dollars to sort of get in the game and get up to speed.
Stephanie Hendrixson 16:02
Yeah, so we've sort of been talking about like the positives from data security, cybersecurity, data around additive manufacturing. But I want to get to like the dark side of data, the things that can go wrong. I think we should talk about that in the second half.
Tim Simpson 16:15
Sounds good.
Jodee McElfresh 16:18
This episode of AM Radio is brought to you by Formnext Forum Austin, a new Formnext event coming to the US this summer. The Conference and Expo is organized by Mesago Messe Frankfurt, AMT--The Association For Manufacturing Technology, and Gardner Business Media, the publisher of Additive Manufacturing Media. Formnext Forum Austin is designed for leaders and owners of manufacturing enterprises, including companies already advancing with additive and those getting ready to adopt it. It's also for engineers engaging with additive technology, and researchers who are advancing what is possible for AM to do. The conference program offers three tracks: production, powered by The Cool Parts Show; design for additive manufacturing, powered by CIMP3D; and technology, powered by Additive Manufacturing Media. The event also includes an expo featuring AM technology, tours of local additive manufacturers and plenty of networking opportunities. And don't miss the finalists of The Cool Parta Showcase, a contest highlighting innovative 3D printed parts. Join Additive Manufacturing Media for Formnext Forum, August 28 through the 30 in Austin, Texas. Find more information about exhibiting, attending or sponsoring this event at Formnextforum.com.
Stephanie Hendrixson 17:38
And we're back. I'm Stephanie Hendrixson. Talking with Tim Simpson about cybersecurity, data assurance, all this good stuff with additive manufacturing. And the first half of the show, we sort of talked about some of the positives, you know, what are the some of the things you can do with data, if you figure out you know, how to track it, how to share it securely? And for the second part of the show, I want to talk about what are the vulnerabilities? What are the different places where your data could be exposed? And maybe what are some things that people can do to protect their data, their information.
Tim Simpson 18:08
The dark side of data, we need a maniacal laugh now, wahaha.
Stephanie Hendrixson 18:14
I'll see what I can do in editing on that.
Tim Simpson 18:16
Right.
Stephanie Hendrixson 18:17
So maybe the natural place to start is kind of the design of the part. I think that's what a lot of us think of first off when you're talking about trying to protect information.
Tim Simpson 18:26
Yeah, I mean, if you look at the definition for additive manufacturing, right, we're making parts layer by layer from 3D model data. And so we're literally starting from that data. Now, traditionally, a CAD file, unfortunately, still slicing that up into to STLs and triangles and converting it into process parameters and tool paths and whatnot. But you know, even within that you've got the data for your part itself, got the conversion of that data, you know, often an intermediate step, STL, to then something that your printer preparation, part preparation software can orient, slice supports, etc. You then actually have the tool paths that have all the laser and process settings, feeds and speeds, so to speak for the different additive processes. And each time that you have different build preparation software, different slicing software, change some parameters, right. I don't think we spend enough time even just talking about version control. Oh, yeah. Of all, all of that downstream data, right? We're sort of used to doing version control for CAD files on our part data. But what about for your slice data? What about for your process parameter data? Do you have a as-designed file versus an as-printed file versus, you know, something else? And so you've got all sorts of new file formats here potentially, that need to be secured, need to be tracked, version control and everything else that we're used to doing with traditional processes, and we're still trying to standardize and formalize in some additive cases?
Stephanie Hendrixson 20:00
Yeah, I think the interesting thing about that is there are nefarious things that can happen with all of this stuff, right? Somebody could get in and tamper with your, with your CAD design, tamper with your STL. Maybe go in and mess with your support structures, that seems like the most tedious and boring way of doing it. But there's also just ways that you could be working with old information like there could be nothing nefarious happening at all, it's just somebody's working with an old version of that design, or there are ways that things can go off the rails without any bad actors involved whatsoever.
Tim Simpson 20:32
Absolutely right. Even just somebody changes, changes one of their parameter settings for their tessellation, right, and you've got potentially a very different part that is now coming out in your STL file versus what you what you thought you had originally. And there have actually been a couple of examples out there, right, where people have gone in and demonstrated that they can hack an STL file that then leads to a bad print, you know, internal to a part for example, there was a drone project, DR0WNED I think was the, the YouTube link there, I remember seeing that where they showed going in hacking the STL file, changing it a little bit, printing out the part, flying the drone, and then, you know, it was the one of the rotors that then of course, wasn't strong enough, once it got up to speed and boom, the drone falls out of the sky and crashes. So this, this can, can be done.
Stephanie Hendrixson 21:24
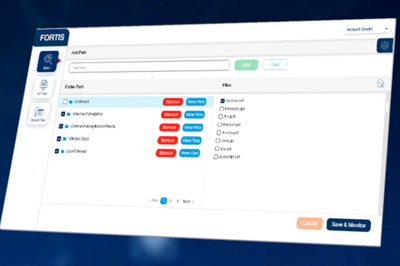
Yeah, we'll put a link to that in the, in the show notes. This is something that VeriTX is now really looking at. So I mentioned like they kind of shifted away from the digital marketplace idea to more protecting individual pieces of data. And so they've launched this product that's called Fortis. And it's basically a way of applying blockchain to protect individual part files, which I, which I think could just be the STL. But it could also include like print parameters and stuff like that. And they sort of see two use cases for it. There's the users that want to protect their internal data. So I think one of their early customers is like a 3D scanning company. And so they've got all these scans that they need to keep safe. But they also want to enable like the safe sharing of data. And so the way that their platform is set up, it's like any sort of change that happens to the file, the sender and the receiver are going to get notified about it. And like if the sender can't account for the change that has happened, then they know like something has been tampered with, like something about the file isn't right. And so don't go forward with producing it. And it's to protect against stuff like that, if somebody were to manipulate the file or or change something about it, you would get notified. It's kind of like just that extra level of security to say like, Hey, something is different. Was this intentional or not?
Tim Simpson 22:38
Yeah, no, there was a great, great study a few years ago, Chris Williams at Virginia Tech did with students in his 3D printing class where they were actually printing dog bone specimens. And unbeknownst to the students, Chris's TA had hacked one of the STL files, and so printed an internal defect, didn't even think about it. And then of course, the students are then running the tests, and noticed, 'Hey, this, this one part really failed early for', and then asked them well, what do you think happened and not a single one of them, if I recall, went all the way back to the STL file being manipulated, right? They thought, Oh, it was just a printer setting was wrong, or just the material didn't go or bla bla bla. And so even students here in a 3D printing course learning about this, they're thinking much more on the process and the material side, they're not necessarily thinking on, on the design and the data side, which is I think, really where these new vulnerabilities lie.
Stephanie Hendrixson 23:31
Yeah. And that kind of ties back to some of the stuff we talked about earlier with like monitoring your printer. So if you could rule out the fact that okay, it wasn't a printer issue, it wasn't a material issue. Let's go back to the design, like you might get through that kind of troubleshooting logic a little bit faster. If we have these other systems in place. It's kind of a safeguard.
Tim Simpson 23:50
Yeah. And so there's, there's a lot of efforts right now, as you know, right, going on with looking at in situ monitoring sensor data, let's take pictures, let's monitor temperatures, let's look at heat profiles, let's look at melt pools, you know, all of these sorts of things, trying to, again, provide data to ensure that we're making the correct material, and then we're making the correct, you know, features and dimensions for whatever part that we're printing. And so having, having that data during the process provides that extra level of trust that we've been talking about.
Stephanie Hendrixson 24:25
So we've talked about the part file, we've talked about the printer itself, there are also ways that people are trying to secure the part like through anti-counterfeiting through authentication methods. And I wonder like, what are some examples of that that you might have seen?
Tim Simpson 24:39
Yeah, I think this is an up and coming area. We've dabbled in a little bit here. But I saw within the most recent ANSI additive manufacturing standards, collaboration efforts, right, trying to have some provisions in there on anti-counterfeiting, basically tagging and tracking of parts. I think that's, that's a concern with all of the pressures on supply chains these days. Is that, 'Oh, somebody could just scan a part and turn around and print it.' Well, how do you then authenticate the part. We worked with Sharon Flank several years ago at InfraTrac, where we were actually embedding as we were printing. So using directed energy deposition, right, a process where we can print multiple materials, we're actually printing a titanium material and then able to actually print a different material within that to create a unique signature. So when you were then scanning it, or X-raying it, it would light up and say, yep, this, this is a different material, which then you could use to authenticate your part, right? We've seen people embedding QR codes and other aspects. We've been working with the company Shape Operating Systems, where we're embedding shape tags and parts. And so you're starting to see all sorts of new ways of trying to use additive to authenticate the part that it's, that it's building.
Stephanie Hendrixson 25:54
So as we've been talking about, like, there are some ways that additive is maybe more exposed to attacks, but it also makes possible some of these really interesting inclusions like you can add things to your part design that is going to serve as a way of authenticating it down the line. And like that's not something that's necessarily going to be possible with other types of manufacturing. So that's pretty exciting, actually.
Tim Simpson 26:14
Yeah, the ability for covert markings, so to speak, right, that you couldn't see on the outside, right, because we're building layer by layer, 'Oh, hey, on layer, you know, layer five, I'm going to put a little marking, and then I'm going to continue to build up my part there.' But then, of course, now, how do we see inside? Well, we need to do an X-ray. So there's, it's not an easy solution, right. But there are ways to go about and attack this. And now even with powder bed fusion, right, we're starting to see multi-material powder bed fusion options, of course, DED, multiple different ways of getting at multi materials with polymer processes as well. And so I think, as I said, there are no standards currently around this. And it's good to see within the America Makes and ANSI effort to at least start identifying it as a gap where we need standards going forward. So I think this is going to be really an exploding area in the next couple of years here.
Stephanie Hendrixson 27:05
Yeah, as you were talking about that, that reminded me in 2021, we ran The Cool Parts Showcase for the first time where we invited people to send in their, their cool parts. And we ran this contest. And one of the entries was from Fabrisonic. So different type of manufacturing, ultrasonic additive manufacturing. And they had 3D printed basically a barcode, and it was multi material. It was copper, and one or maybe multiple materials. But yeah, they were exploring this idea, too. So I think all these different processes, like there are probably different approaches you need to take depending on the 3D printing technique that you're using. But yeah, really exciting to see what people are coming up with there.
Tim Simpson 27:42
To take that even one more, there's actually even, you look at Smart Parts, for example, were actually embedding nanoparticles right in the material itself. So in the powder, that then can be after, you know, it goes through the process. And afterwards, we radiate the part and lights refracted in a certain way to confirm yep, this, this was made with that material. And so now people are figuring out, not only in the process itself, how can we use that to authenticate, but how do we authenticate the materials that were used to print those parts? It's not cybersecurity, right. But that's another vulnerability. If I don't have the right material going into the machine, for example, then my, my chemistry, my composition might be a little off. So therefore, the microstructure and material properties could be completely off. And so it's not just the printing, right? It's the materials as well as that data file that all has to be secure from start to finish.
Stephanie Hendrixson 28:36
So I'm curious like you run a fairly significant 3D printing facility at Penn State. Is this something that you are thinking about? And what types of maybe measures are you taking to protect against that?
Tim Simpson 28:50
No, great, great question. Yeah, we are.
Stephanie Hendrixson 28:53
Well, aside from the professors that are intentionally messing with their students to see if they catch it.
Tim Simpson 28:59
Right. Well, some people are trying to do that. No, no, we've actually started a, as part of our additive manufacturing in design, the online grad program and resident program, we actually have a cybersecurity course. And so over the years, sort of the lessons learned and experiences and things, so we put together a whole two-credit class on that. So we're fortunate within our labs CIMP3D is actually run out of the Clyde Research Lab, lead director is there. And so this is a university affiliated research center with the Navy. So we've already got pretty strict protocols there around IT and cybersecurity and stuff. And so those have been carried through into the lab, we have swipe card access to limit who can get in there. Actually, none of our 3D printers are directly connected to the internet, right? So think it's an air gap, right? If you were to get through the network, you can't actually hack the printer there. But that then means we've had to set up protocols for okay as we're coming in bringing things on a USB drive, you know, how do we get the files onto the machines if somebody's coming in and doing preventive maintenance, right, we're following him or her in there and have observers on board. So yeah, there's, there's a whole set of protocols that we put in place over the years for, for doing this, even then, of course, makes it very tough to get all of our data off of the machines, right, to putting four to eight terabytes on a USB drive takes forever. We've had to, had to come up with some some hacks and whatnot there. But you know, and I think this is something a lot of manufacturing companies I've seen over the years now, the number of reported cyber attacks within manufacturing firms continues to be on the rise. And a conventional, you know, machine shop job shop that's used to running you know, mills, lathes and traditional things is not necessarily cybersecurity may not be first and foremost on their mind, all of a sudden, they're now putting in a 3D printer and plugging it in, and it's connected the internet and boom, all of a sudden, their factory gets hacked. And so raising the awareness, I think that's probably a benefit of additive in these discussions is, hey, as you go digital, there are new things that you need to worry about. Yes, there's new data, you can get to assure that everything's going properly. But at the same time, there's all these other threats and vulnerabilities now that that you need to be aware of and keep track of.
Stephanie Hendrixson 31:19
Yeah, so I think we're coming to the end of our time today. But any last words, any, any advice for additive manufacturing users about how to secure their operations, how to protect their data?
Tim Simpson 31:31
I think a lot of this stuff certainly sounds pretty scary. And it's easy to blow up, you know, take one or two examples and sort of blow it up. And it's like, oh, this is going to affect everyone and everything, right. But I'm very hopeful with the solutions that are starting to come forward now in the data security, cybersecurity regulations. You look again, to NIST, a lot of what they've been doing with their data schemas, their fair practices and the workshops, they've haven't actually had one for small and midsize manufacturers, right. And so tapping into those resources, there's information out there, it doesn't have to be overwhelming. Start with baby steps, right? You're not necessarily going to jump in with both feet. So take your time and approach to it with data just like you do with the process itself.
Stephanie Hendrixson 32:15
All right. Good advice. We will put links to the things that we talked about in the show notes today. Tim, thank you so much for joining me.
Tim Simpson 32:21
Great to be back. Thank you.
Stephanie Hendrixson 32:23
If you like AM Radio, please make sure to subscribe on your favorite podcast platform, give us a five-star rating and tell a friend about the show. Tell a coworker, a colleague, anyone who might be interested in diving a little bit deeper into what's going on in additive manufacturing. And if you want more AM applications, news, insights in the meantime, you can sign up for The BuildUp. That is our twice weekly newsletter, where we are sharing original reporting and writing you can sign up for that at AdditiveManufacturing.Media. Thanks for listening. AM radio is recorded with help from Austin Grogan. The show is edited by Jodee McElfresh and me, Stephanie Hendrixson. Our artwork is by Kate Schrand. AM Radio and Additive Manufacturing Media are products of Gardner Business Media, located in the Queen City, Cincinnati, Ohio. I'm Stephanie Hendrixson. Thanks for listening.
Related Content
-
Decentralized Manufacturing Network Aims to Make 3D Printers a Shared Global Resource
The 3DOS additive manufacturing network will let OEMs and creators take advantage of open 3D printer capacity anywhere in the world.
-
3D Printed Cutting Tool for Large Transmission Part: The Cool Parts Show Bonus
A boring tool that was once 30 kg challenged the performance of the machining center using it. The replacement tool is 11.5 kg, and more efficient as well, thanks to generative design.
-
Carnegie Mellon Helps Industry, Students Prepare for a Manufacturing Future with AM and AI
Work underway at the university’s Next Manufacturing Center and Manufacturing Futures Institute is helping industrial additive manufacturers achieve success today, while applying artificial intelligence, surrogate modeling and more to solve the problems of the future.
Related Content
Decentralized Manufacturing Network Aims to Make 3D Printers a Shared Global Resource
The 3DOS additive manufacturing network will let OEMs and creators take advantage of open 3D printer capacity anywhere in the world.
Read More3D Printed Cutting Tool for Large Transmission Part: The Cool Parts Show Bonus
A boring tool that was once 30 kg challenged the performance of the machining center using it. The replacement tool is 11.5 kg, and more efficient as well, thanks to generative design.
Read MoreCarnegie Mellon Helps Industry, Students Prepare for a Manufacturing Future with AM and AI
Work underway at the university’s Next Manufacturing Center and Manufacturing Futures Institute is helping industrial additive manufacturers achieve success today, while applying artificial intelligence, surrogate modeling and more to solve the problems of the future.
Read MoreUser-Friendly Mass Spectrometry Tool to Enable AM
The Massbox is a technology designed to simplify mass spectrometry by bypassing the need to send samples to the lab for characterization and testing purposes. Exum Instruments’ debut tool is suitable for AM as it can assist with quality assurance, material characterization and failure analysis.
Read MoreRead Next
Platform Backed by Blockchain Provides Data Assurance for Additive Manufacturing
VeriTX’s Fortis platform offers “data assurance as a service” to protect digital information from tampering. The product is launching with an initial focus on files intended for 3D printing.
Read MoreWill Control Over Part Data Expand and Simplify AM Supply Chains?
Digital rights management for manufactured part files will enable OEMs to enforce manufacturing requirements at a distance, potentially providing an alternative to closely held relationships with suppliers of critical AM parts.
Read MoreThe DOE-Funded Institute Working to Make Manufacturing More Secure
National research institute CyManII is working to protect U.S. manufacturing competitiveness, with efforts that touch on training, energy efficiency and cybersecurity.
Read More
.jpg;width=70;height=70;mode=crop)